HL7 for Splunk
Gather and index HL7, EHR, and X12 data into a single view.
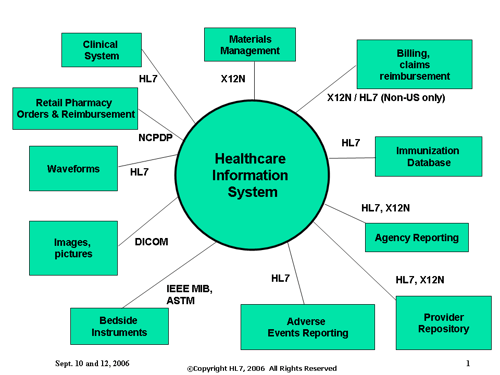
Manage HL7 messages.
The volume of data within the healthcare IT infrastructure is staggering: electronic health record (EHR) systems, HL7 messaging, X12 billing data and connected medical devices, not to mention application servers, mobile devices, web servers, virtualized servers, portals, billing systems and claims management systems—all of this data is critical in order to offer consistent, efficient, and high-quality medical care.
Splunk allows healthcare organizations to gather and index all of this data—both real-time and historical—and offer operational intelligence across the entire healthcare IT ecosystem. Conducive makes this even easier with the HL7 app for Splunk, which allows you to build a single and accurate view of patient and provider messages across your entire healthcare infrastructure.

The HL7 App for Splunk allows you to:
- Perform healthcare analytics on one or more EHRs using information contained in HL7 messages
- Search and correlate HL7 messages across multiple environments with an easy-to-use interface
- Validate HL7 messages during implementation and in production
- Reduce ramp-up time during implementation
- Search and debug problems with messages
- Convert delimited HL7 messages into an easy-to-read JSON format with message drill-down
Insights from Our Blog

Conducive Launches AppWatch
Conducive Consulting announces the launch of AppWatch, a new observability platform designed specifically for city and county IT teams. AppWatch delivers real-time visibility into critical systems—servers, networks, and applications—without the complexity or cost of traditional enterprise tools. With a lightweight setup, proactive alerts, and a unified monitoring dashboard, AppWatch helps municipal IT teams maintain uptime and support essential public services with minimal overhead.
Read More
Conducive Consulting Secures 2024 Splunk Public Sector Emerging Partner of the Year
Conducive Consulting secures 2024 Splunk Regional Partner Award for outstanding performance and commitment to their Splunk partnership in the public sector.
Read More
Improving OT Security in Water and Sewer Districts with Splunk Edge Hub
Enhance OT security in water and sewer districts with Splunk Edge Hub. Discover how real-time data analysis and comprehensive threat detection can improve operational efficiency. Download our white paper for more insights.
Read More